F5 Breach Puts Enterprises on Edge

It’s every cybersecurity vendor’s worst nightmare: A data breach exposes vulnerabilities in products meant to protect customer security. But that's just the scenario facing application security provider F5. According to the vendor’s report:
“In August 2025, we learned a highly sophisticated nation-state threat actor maintained long-term, persistent access to, and downloaded files from, certain F5 systems. These systems included our BIG-IP product development environment and engineering knowledge management platforms. We have taken extensive actions to contain the threat actor. Since beginning these activities, we have not seen any new unauthorized activity, and we believe our containment efforts have been successful.”
Various sources reported that the threat came from state-backed Chinese spies, who were said to have lurked inside F5’s network since 2023. Once F5 found the hack, it delayed revealing it publicly, apparently while it crafted the updates required to protect the affected products. In an SEC filing dated October 15, F5 reported that on “September 12, 2025, the U.S. Department of Justice determined that a delay in public disclosure was warranted pursuant to Item 1.05(c) of Form 8-K. F5 is now filing this report in a timely manner.” That item on the SEC form specifies that delays in filing a public disclosure are allowed in cases where reporting the situation would involve “a substantial risk to national security or public safety.”
Corresponding to F5’s formal revelation on October 15, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on that date issued an Emergency Directive advising government agencies to immediately “inventory F5 BIG-IP products, evaluate if the networked management interfaces are accessible from the public internet, and apply updates from F5. CISA’s directive states: “This cyber threat actor presents an imminent threat to federal networks using F5 devices and software.”
F5’s updates are extensive and apply across its product line. Whether the government agencies affected remain open in view of the shutdown and were able to apply the updates isn’t clear.
A Widespread Ripple Effect
The breach threatens to have a massive ripple effect. As noted above, source code from F5’s BIG-IP Application Delivery and Security Platform was compromised, and that platform features load balancing, DNS services, Web application and API protection, and a range of other services, as illustrated below:
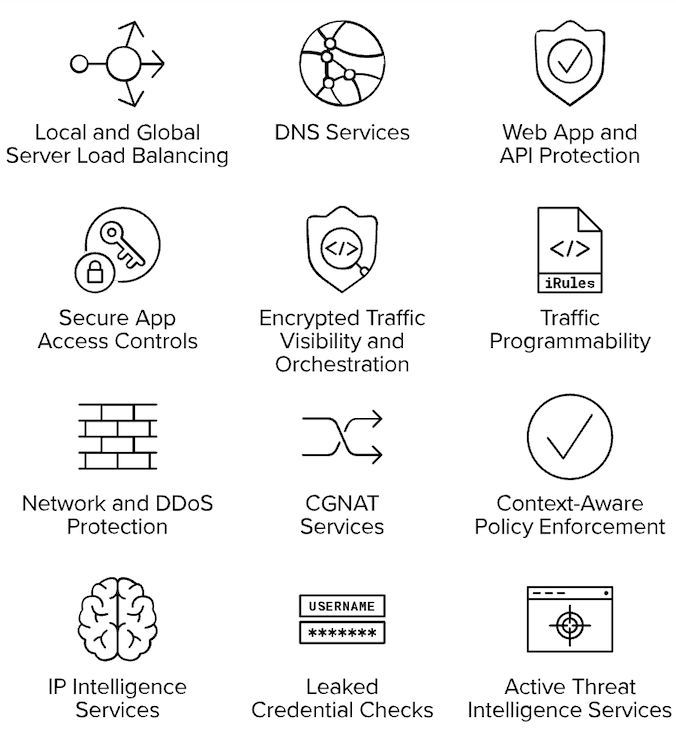
BIG-IP Features and Functions. Source: F5
Observers have compared the breach to the SolarWinds hack five years ago, which resulted in SolarWinds exit from the public markets and its reformation as a private company. But this may be even larger in impact. F5’s development platform could affect a broad range of large enterprise customers and telcos. The F5 breach also has direct implications for SASE (Secure Access Service Edge) and network-infrastructure layers, since many SASE deployments rely on vendor modules such as those from F5.
The F5 website states that the vendor is “trusted by 85% of the Fortune 500.” A recent Q3 2025 earnings presentation shows the enterprise sector accounting for 70% of F5 product bookings, with government and service provider customers taking 15% each. Customers include Viettel, the Scottish Government, the American University in Cairo, and other unnamed government, airline, and telco customers.
F5 also boasts an impressive raft of technology partners, which integrate F5 products as part of their services. AWS, Google Cloud, and Microsoft Azure are listed here, as well as Arista, Cisco, Dell, Equinix, HPE, Nutanix, NVIDIA, and Red Hat, among others.
Weirdly, the this week's AWS breach was blamed in part on faulty DNS resolution, a key service of the BIG-IP platform. While this could be purely coincidence, it points to the many questions arising from F5’s ongoing security crisis.
Timing Follows AI Acquisition
Although there really is no good time, the massive breach comes at a bad time for F5, which recently announced plans to acquire CalypsoAI, an AI-focused cybersecurity company with a real-time threat defense platform. Futuriom sees the move as potentially elevating F5 as one of the top providers of networking and security infrastructure for the new AI-driven world. Also, F5's focus on API security, along with multicloud and hybrid infrastructure support and AI, has been especially interesting. But this will have at least short-term impact on its brand.
F5 has also been riding a wave of financial success. Its latest quarter showed $780 million in non-GAAP sales, up 12% year-over-year (y/y). Adjusted EPS grew 24% y/y to $4.16. Gross margin was 83.1%. But this week's attack has put its share price under pressure.
F5 must now overcome the damage. Over the past several days, the vendor’s stock has plunged. The share price is down 10% this. month.
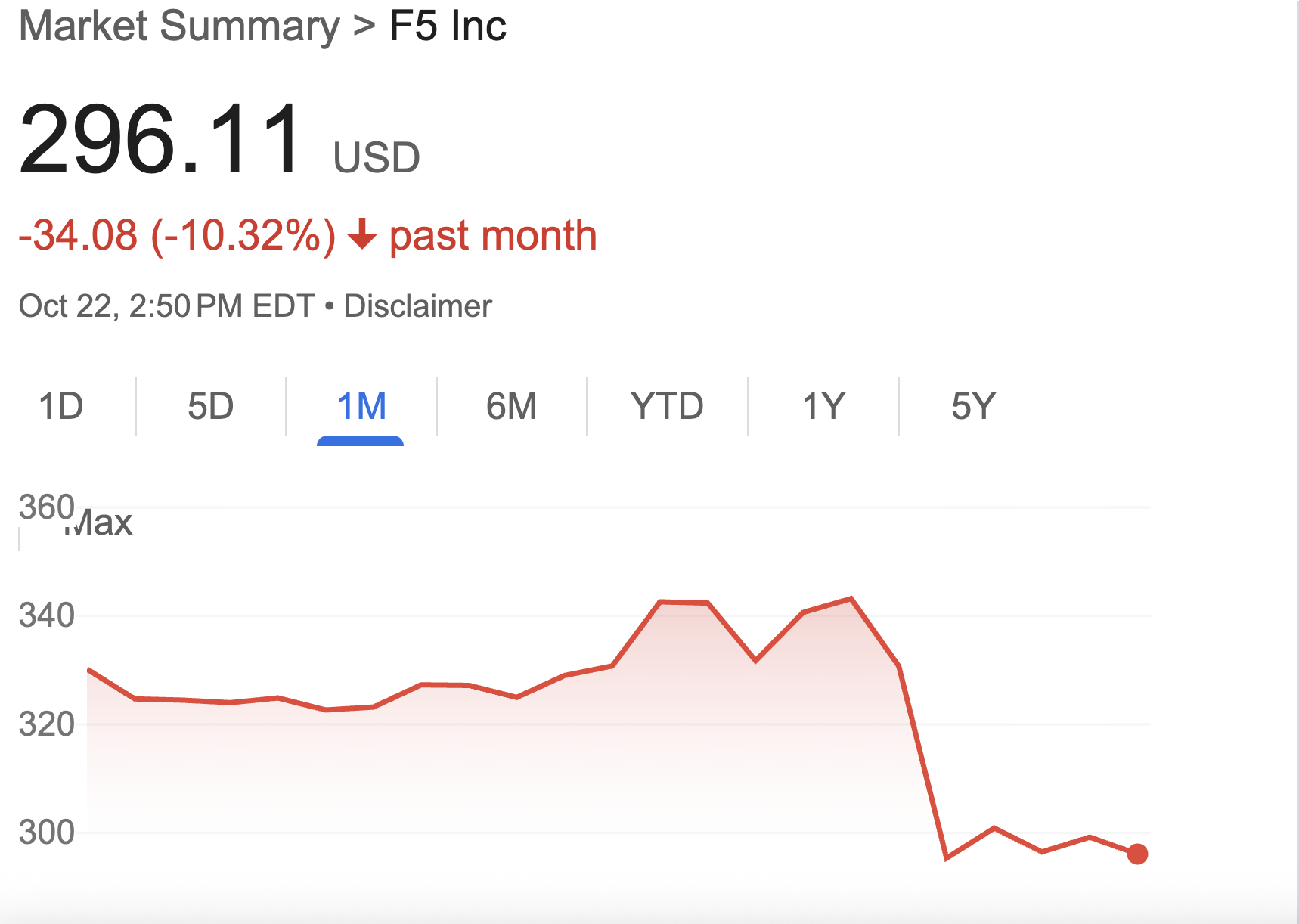
Source: Google
Note that F5 will release its quarterly earnings report on Monday, October 27, after market close.
Other major cybersecurity vendors have experienced major attacks and fumbles in the past but managed to recover. Major endpoint security vendor CrowdStrike famously issued a flawed update in 2024, causing a global IT outage. It was not a hack, but it was a major mistake that had global impacts. CrowdStrike's shares later recovered to a new high.
Solar Winds survived its own attack before later being acquired by private equity. F5 is a much larger company and its infrastructure is pervasive.
Ironically but to its credit, F5 has turned for help with ameliorating the threat to companies against which it competes in some areas, including CrowdStrike, Google’s Mandiant, NCC Group, and IOActive. And clearly, the firm will need all the help it can get to turn a potential tide of trouble.
Futuriom Take: The breach of F5's network is stunning in its breadth and duration. While the full impact of it remains to be seen, F5 is positioned well to face the challenge, whatever the outcome. But cybersecurity and networking companies have proven that a full recovery from such events is feasible.