Behind the SolarWinds Debacle

The hacking of SolarWinds (SWI) net management software Orion continues to ripple through cyberspace, stirring up evidence of a lengthening list of victims and raising the question of how affected entities, including SolarWinds, can survive the attacks.
When SolarWinds revealed the hack in an SEC filing December 14, it acknowledged “a highly sophisticated, targeted and manual supply chain attack by an outside nation state,” now generally thought to be associated with Russian intelligence. The company estimated that 18,000 of its 33,000 Orion customers were affected.
Now it looks as though many, many more customers who received Orion software updates within the period from March to June 2020 have been hacked by what is widely termed Solorigate. Further, hundreds of U.S. government agencies were targeted by the malfactors. An article in the Federal News Network cites a statement by the U.S. Cybersecurity and Infrastructure Security Agency (CISA):
“The SolarWinds Orion supply chain compromise is not the only initial infection vector this APT [advanced persistent threat] actor leveraged…. CISA is aware of compromises, which began at least as early as March 2020, at U.S. government agencies, critical infrastructure entities, and private sector organizations by an APT actor.”
Microsoft and CrowdStrike Attacked
Besides the widely publicized numerous U.S. government and private sector victims of Solorigate, Microsoft (MSFT) acknowledged last week that the supply chain intrusion turned up in its source code repositories.
Microsoft said the hack was “related to the SolarWinds Orion platform." The hack was contained and remediated, Microsoft said, with no clear evidence that associated (and unidentified) products were tampered with, or that any customer or partner information was compromised.
Still, the long-range impact of the hack on Microsoft is horrible to consider. (What about Azure? What about the range of Secure Edge and SASE wares that support Microsoft products?) One company, CrowdStrike (CRWD), for instance, was told by Microsoft on December 15 that a Microsoft reseller’s account had been used earlier in 2020 to read CrowdStrike emails.
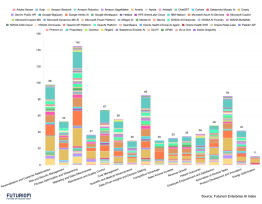
The CrowdStrike example demonstrates the intricate interconnections and awful potentialities of Solorigate on customers of attacked tech firms such as Belkin, Cisco (CSCO), Intel (INTC), NVIDIA (NVDA), VMware (VMW), and of course FireEye (FEYE), which caught the hack and publicized the specifics on December 13.
SolarWinds in the Hotseat
While not the only unwitting transmitter of the APT, SolarWinds has become its poster child. Since a large portion of the attack originated as a “trojanization” of one of Orion’s automated software build programs, SolarWinds has been raked over the coals. A recent New York Times analysis included several key points:
— SolarWinds overlooked security. According to the New York Times, SolarWinds CEO Kevin Thompson put security on a back burner. And in an effort to reduce operating costs, the company offloaded software engineering to remote offices in Eastern Europe, where Russian intelligence may have more easily penetrated.
— SolarWinds ignored warnings. The Times article cites employees and former advisors as saying SolarWinds ignored advice to upgrade its security functions on Orion and other products.
— SolarWinds did not immediately stop the hack. According to the Times, experts say the company continued to sell hacked software for days after it became aware of the invasion.
Can SolarWinds Survive?
Since the hack, SolarWinds has provided patches for Orion. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has ordered all federal agencies to adopt the fixes or stop using the software.
Also, the company seems to be pursuing two plans that could aid its tarnished reputation. First, SolarWinds CEO Kevin Thompson is stepping aside for Sudhakar Ramakrishna (ex-Pulse Secure)— a move that was planned before the hack was exposed. Second, the company plans to spin off the managed service provider portion of its business, which does not include Orion, into a separate publicly traded entity named N-able. This move could distance the company from Orion, which probably has a complete makeover in its future.
Enter the Competition
The recent hack may become a market boon, especially for SolarWinds Orion customers looking elsewhere for help with automated network monitoring. According to Gartner, competitors include privately held security information and event management (SIEM) vendor ManageEngine as well as VMware, open-source Nagios, and Microsoft, along with many others.
The U.S. government may have a more arduous road to recovery. The attackers managed to get around a range of homegrown government cybersecurity solutions, including CISA’s costly Einstein system. And the New York Times quoted experts as saying that many government systems may have to be ripped and replaced in order to withstand further attacks.
Whether public or private, entities affected by Solorigate and the malware offshoots it’s spawned have months of work ahead. The extent of repairs will be measured in part by the number of affected companies and agencies that continue to surface.