How Is Security Applied to the Internet of Things?

The Internet of Things (IoT) and the Industrial IoT (IIoT) are spreading quickly, as digital transformation enables automation in a variety of environments. The benefits of streamlining applications and enabling ones that formerly were impossible has fueled ongoing expansion. And the trend will only gain momentum as the mobile edge cloud emerges.
But the rewards of IoT/IIoT come at a price: The proliferation of sensors or software embedded in industrial equipment, smart-city applications, retail items, thermostats or water meters, and other gear widens the attack vectors for all these smart devices and anything connected to them.
And the situation will only get more critical. Already estimated at roughly 10 billion, the number of IoT endpoints is anticipated to reach 21.5 billion by 2025. The rise of 5G will catalyze the trend.
In order to secure these IoT/IIoT networks, it's important to scope out their fundamental architectural elements in order to shield them from malware, distributed denial of service (DDoS) attacks, ransomware, bots, and more. Below is a general outline of what must be protected:
The network. Data on connected devices must be sent to an application, whether that resides in the public/private/hybrid cloud or data center. Since traversing any network puts data at risk, edge compute is the strategy of choice for IoT/IIoT. The idea is that only the data necessary for the application need be sent over the network; most information doesn’t need to leave the factory, oil rig, campus, equipment closet, or branch network. This not only keeps data secure, it also boosts performance levels and saves connection costs.
The cloud edge. This is the portion of the environment where cloud network meets remote site, and typically it is protected by systemic security offered by cloud provider(s) or an enterprise data center. Still, systems differ in their abilities to expose risk and remediate problems for network endpoints. All the automation and artificial intelligence (AI) aimed at security by a particular solution may still not clarify what’s happening in IoT/IIoT.
In addition to existing systems for infrastructure security, services are emerging that combine the solutions of more than one vendor, furnishing integrated and more comprehensive security for IIoT/IIoT. Integrators and tech consultancies are active in this area, helping bring together technologies that can ensure that security extends to the farthest reaches of the network.
The device edge. Endpoint security is focused on providing more information about IoT/IIoT devices for security applications. There also are tools that protect access to devices and restrict devices from interacting with unknown applications or URLs. In some instances, security is provided at the chip level, within sensors, which is set to interact with gear or software at the infrastructure edge. Elsewhere, routers and secure access service edge (SASE) solutions ensure the attached endpoints are secured.
The diagram below offers a very simplified view of the segments of IoT architecture. In this case, the application is a home thermostat, but the portions of the network could be applied to sensors associated with a range of business and industrial applications.
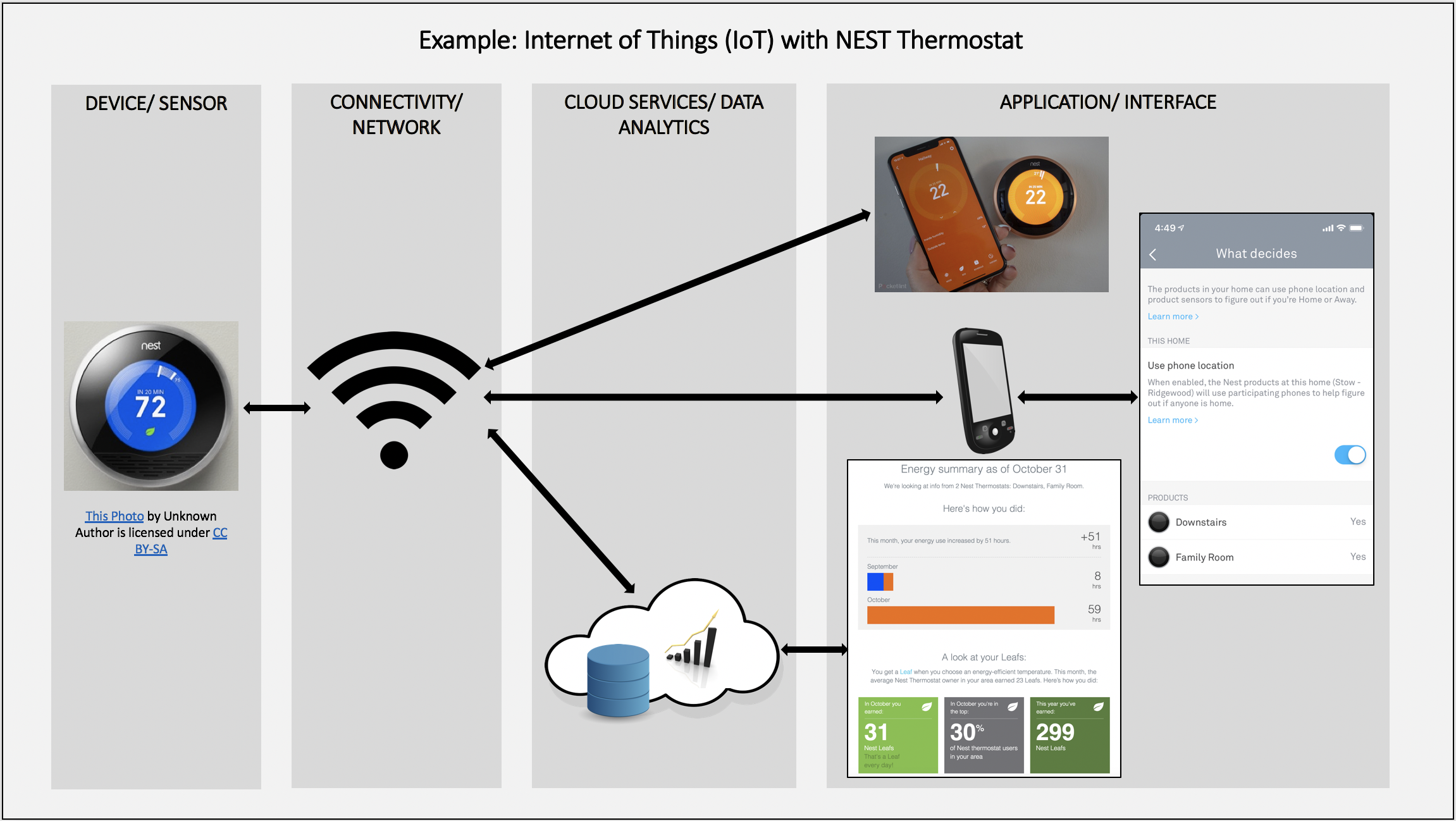
Source: Leenaborbarua, CC BY-SA 4.0 , via Wikimedia Commons
Things to Watch for in IoT/IIoT Security
One key to making the most of any security plan for IoT/IIoT is to ensure that each device in every branch, remote site, campus, and home end point is accounted for by the system. So-called shadow IoT, meaning devices attached to the network that weren’t assigned or registered by IT, can become vulnerabilities. These devices may include home laptops or tablets, fitness gear, smart home devices, and wireless access points. Leaving these devices blind to the infrastructure security system leaves them — and everything they’re attached to — open to malfactors.
Another helpful tool is the certification of network devices to fit specific IoT/IIoT requirements or standards. This is an area in which channel partners and integrators might help by ensuring devices meet specific security criteria they've established.
Certification protocols also are emerging among industry groups and at the government level. The European Union Agency for Cybersecurity offers a certification of chips for smart passports, bank cards, and other forms of chip-based identification.
In another example, the IoT Cybersecurity Act of 2020, an item of legislation passed in early October by the U.S. House of Representatives, outlines security procedures to be followed by IoT vendors to government agencies. While fairly general, it calls for IoT/IIoT vendors to meet a set of still-to-be-defined standards for security and to publicly report any vulnerabilities and remediations. Stay tuned.
Since IoT/IIoT security involves a range of “moving parts,” it’s not surprising that solutions are plentiful and diverse. Many involve more than one product or service, and partnerships abound. But underpinning any solid strategy is an awareness of the fundamental areas of the IoT/IIoT environment that call for security. Once that awareness is established, there are plenty of options to evaluate.