What Are the Top SASE Use Cases?

With remote as the new norm and as enterprise networks and workforce have become more distributed and virtualized, the Secure Access Service Edge (SASE) model, also known as Zero Trust Edge (ZTE), has taken center stage recently. Digital business and today’s dynamic needs of modern and distributed enterprises require a cloud-delivered model to enable users and deliver secure access to applications and resources regardless of their location at any time. As a result, the convergence of modern networking and Zero Trust security has become a key initiative for many organizations and the interest in adoption of a unified SASE model has become intense.
[Editor's note: This Tech Primer is sponsored by Citrix. For more information on Citrix SASE solutions, please go here.]
Figure shows a unified approach to SASE for the modern enterprise; convergence of networking and security. Source: Citrix
The momentum behind SASE’s ascendance is clear: As an essential element of digital transformation, SASE was gradually emerging for many organizations worldwide a couple of years before the COVID-19 pandemic of 2020. Then, virtually overnight, companies shifted to a predominantly remote workforce, requiring a redesign of corporate networks to meet a host of challenges.
Among the issues: Users' personal unmanaged devices became essential tools for keeping business afloat during lockdowns but were difficult to secure with any consistency. Application performance suffered when legacy virtual private network (VPN) links backhauled exponentially larger amounts of Internet traffic to servers at headquarters. And Internet connections proved unreliable across geographies, hindering collaborative applications and workgroup functions.
Under these conditions, it became apparent that organizations that were taking digital transformation piecemeal would have to pivot more quickly from centralized, premises-based WAN connectivity toward cloud services linked by software-defined wide-area networking (SD-WAN) and equipped with the SASE technology and model.
In the primer that follows, we’ll examine this new enterprise network architecture and see how it ensures not only security for all resources, but optimal employee productivity and better control for IT.
SASE Requirements for the Digital Workspace
To see how the SASE model works in the context of today’s environments, it’s helpful to start with the primary focal point of the corporate network — the end user. This is where the essential work of an organization takes place. And for this work to happen optimally, it helps if the following basic requirements are met:
- Users must have secure access to all the applications and data required to perform the job assigned.
- For each user, access to corporate resources must be appropriate, matching a person’s skills and level of organizational responsibility.
- Users must be able to work from any location — branch office, store, field office, clinic, warehouse, home, or headquarters —across locations, in any geography.
- Users must be able to work on a range of devices.
- Users must be able to work at the speed that matches their thought processes.
- Users must be able to collaborate with others, regardless of location.
- Collaborating users must be able to rely on the same level of network performance, no matter where they are located.
- Users must not risk confidentiality, privacy, or exposing the business to security threats.
As previously noted, meeting these conditions using traditional hub-and-spoke data center networking is difficult at best. Backhauling traffic to central servers behind a firewall reduces application performance. And coping with an ever-growing roster of sophisticated security threats without a unified approach can result in a juggling act of multiple products that are not integrated.
Things don’t get much better when a security service is coupled with local Internet breakout. While latency is reduced by adding cloud-based security, there is no guarantee that applications will perform consistently in the absence of suitable performance controls.
But with cloud services encompassing the SASE model, it is possible to offer a digital and seamless workspace experience capable of meeting all of these needs. Let’s take a closer look.
The Role of SASE in the Digital Workspace
The SASE model is based on SD-WAN and refers to the appliance or point of presence (PoP) located closest to the end user in that network, as illustrated below:
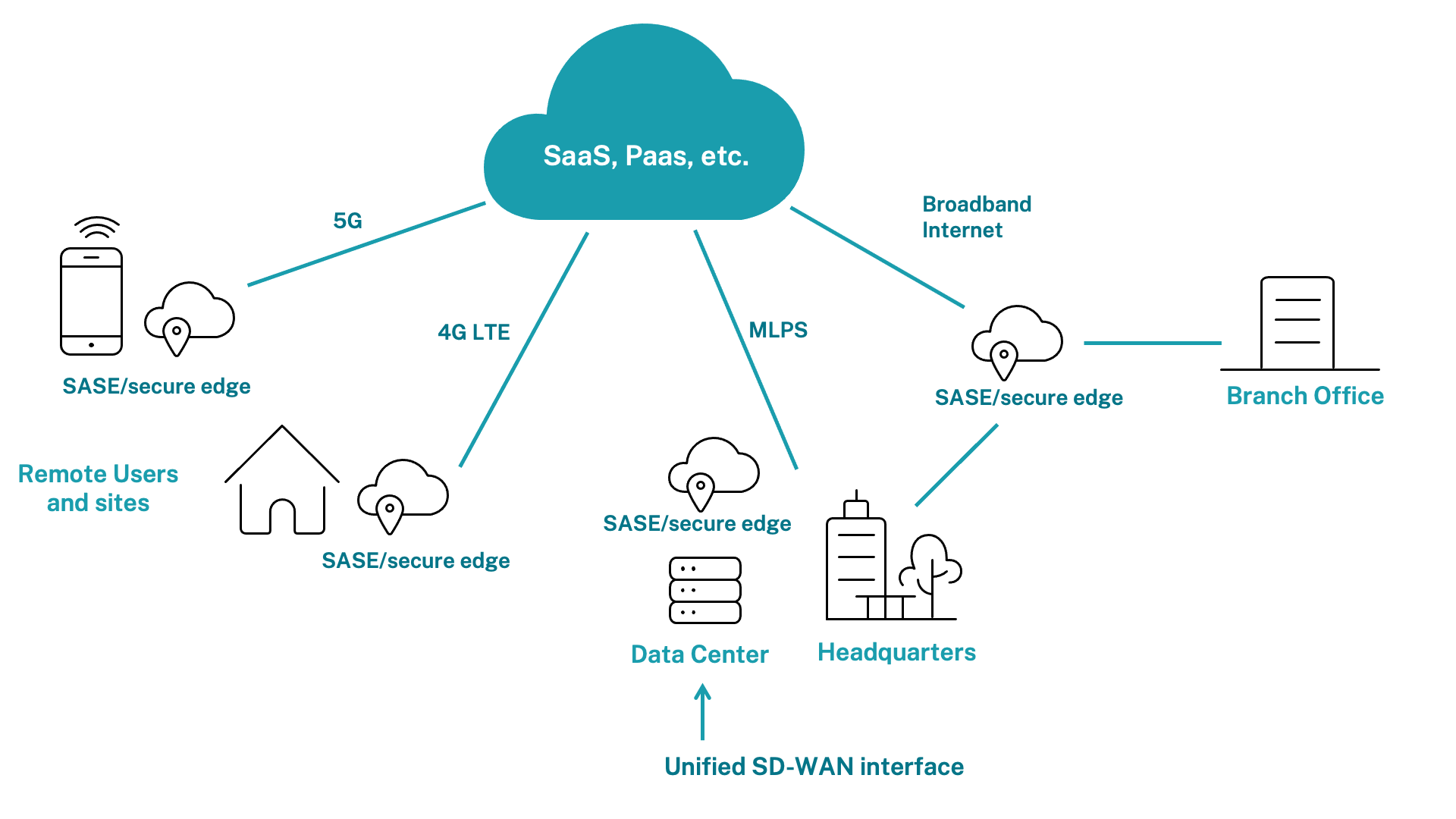
This design makes important innovations possible due to SD-WAN’s nature as a virtual router-replacement technology that separates the control plane from the data plane in wide-area networks.
For instance, the SASE can be integrated with functions that in legacy networks would require extra hardware and software. These include security features such as secure web gateways (SWGs), cloud access security brokers (CASBs), cloud-based “firewall-as-a-service” (FWaaS), and zero trust network access (ZTNA) or software-defined perimeter (SDP) services.
Further, SD-WAN’s architecture makes it possible to add application load balancing or traffic optimization along with advanced security inline. This improves network performance across MPLS and virtualized network segments — for digital workspaces — without requiring any packet-level scrutiny.
With a unified approach to the SASE model, security is embedded into the network architecture, and these advanced features are capable of enabling innumerable and secure digital workspaces linked to cloud services or applications.
How IT Benefits from the SASE Model and the Digital Workspace
SASE isn’t the immediate answer to all IT problems. Moving data to the cloud is no guarantee of security or performance quality. Absent effective orchestration and management processes, marshaling cloud-based resources for masses of remote users can be just as daunting as maintaining security and performance via premises-based servers. And the situation worsens if public cloud services are coupled with on-premises applications in hybrid networks without adequate management.
But deploying unified orchestration and management ensures that the SASE meets specific requirements for safe and smooth cloud service delivery. This benefits IT in the following ways:
- Reduced network complexity. Integrated security and application management for remote workforce eliminate the need for multiple point products, such as secure sockets layer (SSL) VPNs, endpoint management tools, and perimeter firewalls. Besides saving capital costs such as hardware and licensing, this approach saves time and operational costs associated with integrating and managing multiple products.
- Heightened security. Security risks to corporate data increase daily. And as we’ve noted, with more employees working remotely in a “bring your own device” (BYOD) mode, along with increased technology in branch offices and remote sites, the threat surface widens significantly. Comprehensive workspace protection combined with the cloud-enabled SASE/secure edge approach arms IT with the defenses needed to protect an organization’s resources while ensuring employees are able to work where and how they need to.
- Remote site stability. A major benefit of SASE is the ability to quickly connect remote users and branch offices to cloud-based applications without concern for the unreliability, security vulnerabilities, and performance issues associated with local Internet breakout and backhaul. Instead, a well-equipped orchestrator as part of a SASE solution can spin up remote connections to individual users and branches and ensure those connections are safe and delivering consistent performance.
- Application optimization. With hundreds if not thousands of applications on premises and in the cloud, performance can suffer in legacy networks. But SASE allows for the addition of load balancing and automated traffic routing to ensure quality of service (QoS) to users in hybrid cloud environments.
- Multi-cloud connectivity. There are many public services available to enterprises that wish to move applications to the cloud. Legacy approaches often require IT to support multiple service providers on an individual basis, leading to network complexity. But a unified SASE model enables secure access to multi-cloud and hybrid-cloud environments for all remote digital workspaces.
Clearly, SASE networking advances IT success in its mission to deliver data and applications safely to end users. But there is an essential element to the architecture that maximizes security across the board. Let’s take a closer look at ZTNA.
How Zero Trust Fits into the SASE Model
In legacy networks, access to applications and data is granted to users who, from the Internet or corporate network, can present password- and IP address-based authentication to the firewall and/or intrusion prevention system (IPS) that secures centralized servers. This “castle-and-moat” approach means that once inside the firewall, anyone can freely roam corporate resources. If a hacker breaches the HVAC system, for example, they could conceivably access the credit-card repository.
The zero-trust approach stems the flow of errors and attacks by turning this access model on its head. In short, zero-trust access assume that everyone, inside or outside the organization, is not to be trusted unless they present authentication based not on passwords or IP addresses but on criteria such as identity, time of day, location, and appropriate context.
Further, users are permitted “least privilege access” to only the information needed to achieve their specific business goals. IT can grant access to a particular user or group to Microsoft 365, for instance, but not to workspaces outside their immediate geographical area.
ZTNA (Zero Trust Network Access) implementations aren’t restricted to specific technologies. Various methods are deployed to implement the approach, such as multi-factor authentication and the use of one-time passwords or numbers sent to a person’s mobile phone or email. The SASE model offers a platform for implementation of these tighter, policy-based security controls.
Systems designed for ZTNA also can employ machine learning and other techniques to monitor and flag anomalies in real time. A user, for instance, logs into the network with the correct identity but from the wrong country. Or a user qualifies to use the network but is restricted from using it in the “wrong” time zone. The use of analytics builds improved security from a growing roster of threats, which seem to multiply daily. The recent SolarWinds debacle demonstrated the sad truth of the sophistication and subtlety of today’s network attacks.
It is important to note that the ZTNA approach does not rule out the use of multiple security products, which continue to be used in many environments. Still, multiple distinct solutions, while generally effective if sufficiently integrated, can be difficult to corral in the face of zero-day cybersecurity threats.
So any ZTNA implementation should be able to incorporate legacy security systems in SASE orchestration and management. If properly designed, one interface can govern secure access to numerous data sources and applications by virtually unlimited numbers of remote users.
Top SASE Use Cases
There are many reasons to deploy SASE architecture for the modern enterprise environments. But it is by overlaying a unifying orchestration and management interface for both security and networking that optimal benefit accrues. The following are top use cases for this approach:
Rapid response to network demand. The pandemic of 2020 revealed how quickly businesses may need to respond to crises. When thousands of people who had not worked at home suddenly were called to do so, many IT organizations that relied on VPNs were overwhelmed. With a focus on cloud-enabled digital workspaces governed by the SASE model, desktops and applications can be rolled out quickly and rolled back just as fast.
Support for mobile users. Internet of Things (IoT) devices and desktops, along with an increasingly mobile workforce, have challenged IT to keep access secure and wireless performance consistent. And it’s not about users working from the cottage or yacht: As 5G rolls out, branch offices, factories, utility centers, warehouses, and other locations will increase the use of IoT and automated wireless endpoint applications. This calls for the scalability and control a unified SASE model delivers.
VPN replacement. As we’ve noted, VPNs aren’t reliable and secure enough to accommodate cloud access from an exponentially increasing number of remote devices, especially when users use their own smartphones, laptops, and iPads interchangeably. With SASE, digital workspaces managed with zero trust access can replace cumbersome VPNs.
Controlled move to cloud services. Many organizations in multiple vertical markets plan to move their data and applications to the cloud, but not all want to do so at the same pace. With the single-interface management for SASE elements, it’s possible for IT to move as gradually as desired from on-premises to hybrid or multi-cloud environments without sacrificing workspace availability, application performance, or security.
Support for multiple operating systems. The choices available for a SASE environment extend to the operating systems that run within digital workspaces. So enterprises with substantial Linux demand don’t have to move to separate clouds or systems to support their users.
The above use cases illustrate how the SASE advances the underlying efficacy of the corporate network, compared with other approaches, as illustrated below:
Source: Citrix
























