ZTNA Trends and Leaders 2022

Zero trust is one of the hottest buzzwords in cybersecurity circles. It is more a philosophy than a specific technology, but it has important implications for emerging cybersecurity technologies, especially in the networking area, where the applications of the approach are often referred to as zero trust network access (ZTNA).
Because networks and applications are becoming more complex, it’s more important to verify and authenticate users and applications across multiple dimensions. We now have cloud networks, WiFi, Internet of Things (IoT) devices, remote users, and hybrid work. ZTNA technology can be used to track and automate the authentication of devices and people as they use all of these networks and applications, or in many cases travel across clouds or the Internet.
Download the Report Here Now!
What Is ZTNA?
A good base definition of ZTNA comes from the U.S. National Institute of Standards and Technology (NIST), which describes zero trust as: “A collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.“
NIST believes that a zero-trust strategy is “primarily focused on data and service protection but can and should be expanded to include all enterprise assets (devices, infrastructure, components, applications, virtual and cloud components) and subjects (end users, applications and other non-human entities that request information from resources.”
Many ZTNA systems as well as cybersecurity tools function in a similar way: Collect as much data as possible from different sources, then process or analyze that data in a policy engine that can determine if user access is legitimate or a threat. These sources can include:
• User credentials
• Network devices (routers, switches)
• Devices and endpoints
• Log files
• Applications workloads: For example, virtual machines (VMs) or containers
• Cloud or applications data
• API sources such as single sign on (SSO), security information and event management
(SIEM), identity managers, threat intelligence databases
What's in This ZTNA Report?
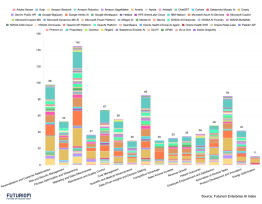
ZTNA has become one of the hottest areas of investment in the cybersecurity market right now, with more than 30 active startups and at least 20 major public cybersecurity companies adding ZTNA products and solutions.
This report gives a general overview of ZTNA architectures and approaches and details the positioning of the major players in the market. The contents include the following:


Companies featured in this report: Akamai, Appgate, Axis Security, Banyan Security, Barracuda, Cato Networks, Cisco, Citrix Systems, Cloudflare, Cyolo, Elisity, Fortinet, Google, Infiot, Illumio, Jamf, Juniper Networks, NetFoundry, Netskope, Okta, Palo Alto Networks, Perimeter 81, Teleport, Versa Networks, VMware, Wandera, Waverly Labs, Zentera Systems, Zscaler