Here Comes Post-Quantum Cryptography

Enterprises worldwide are sitting on a ticking timebomb, experts say. But a growing number of companies are jumping at the chance to help them forestall disaster.
Here’s the challenge: Quantum computing algorithms, thanks to significantly expanded computational capabilities, have the potential to easily crack systems protected by the RSA and ECC algorithms, the two most popular methods of encrypting data online.
These warnings have lingered for decades, but the post-quantum era is now in sight. Google recently published theoretical results showing that a quantum computer with 1 million noisy qubits can break 2,048-bit RSA encryption in one week. That's a larger computer than exists today, but it's also a 20-fold improvement over Google's calculations in 2019. So, while quantum computers getting larger (measured in qubits), the threshold for them to crack conventional encryption is also getting lower.
Within the next several years, as quantum computing emerges, firms will have to take measures to protect their legacy systems—or risk losing data and infrastructure to hackers armed with quantum computing tools.
Post-Quantum Cryptography Emerges
At the recent RSAC in San Francisco, there was noticeably increased interest in post-quantum cryptography (PQC), which refers to encryption techniques that appear resistant to quantum computing attacks.
“There’s a lot of opportunity in helping all of the … end user companies out there with ‘I have to switch out my encryption brain, so provide me with the tools to be agile, so that when I need to do it, I can,’” said RSAC Head of Community Research Laura Koetzie at the conference.
But Koetzie noted that getting ahead of the problem means knowing where to address it. “There is a whole constellation of things. It’s not just … making the post-quantum algorithms themselves available,” she said. Companies will need to know where their encrypted data resides, rank its importance, and proceed to ameliorate the risks. “In addition to the core encryption, there’s a whole load of services around that that are going to be necessary,” Koetzie said.
The Starting Point and Beyond
One company trying to address these needs is Keyfactor, a Cleveland, Ohio-based firm with longstanding presence in the cybersecurity market. Founded in 2001, Keyfactor has gone through a series of iterations, each one augmenting a basic focus on public key infrastructure (PKI) and digital certificate management. Now employing 412 and with a valuation over $1 billion, Keyfactor is positioning itself as a player addressing enterprise PQC needs.
Early in May 2025, Keyfactor purchased InfoSec Global, a startup specializing in cryptographic posture management, for an undisclosed sum. InfoSec provides software that discovers cryptographic assets “across devices, source code, binaries, file systems, applications, cloud workloads, and more,” according to Keyfactor’s press release. InfoSec also provides a comprehensive way to manage all cryptographic assets from multiple IT environments, whether they’re related to legacy systems or post-quantum cryptography.
Keyfactor also bought in May a product called CipherInsights from QuantumXchange, an encryption provider based in Maryland (again, terms not disclosed). Keyfactor intends to integrate both acquisitions into its product line to offer technology for discovering cryptographic assets, managing them, and shifting them to PQC as needed.
Keyfactor also integrates its software with confidential computing from Fortanix and Anjuna for private key protection.
“We’re uniting the best of the best,” stated Keyfactor CEO Jordan Rackie, in the press release. “Together, we’re giving organizations a seamless path to uncover and fix today’s cryptographic risks and get ahead of tomorrow’s quantum threats.”

Jordan Rackie, CEO, Keyfactor. Source: Keyfactor
Other PQC Efforts Underway
Keyfactor isn’t alone in addressing the PQC challenge. Fortanix, for example, offers its own post-quantum readiness products, including discovery of current assets and benchmarking against known post-quantum threats. Note also that for Keyfactor, Fortanix, and others, the discovery step is not a one-time thing. Algorithms, attacks, and policies will all change over time, creating a need to keep watch over an organization's post-quantum stance.
Elsewhere, a crowd of major technology players, including AWS, IBM, Microsoft, and Google, have been working with the National Institute of Standards and Technology (NIST) to create specifications for replacing ECC and RSA with cryptography that is more resistant to quantum computing-based attacks. In August 2024, NIST released the first three encryption algorithms designed, as NIST puts it, to “withstand cyberattacks from a quantum computer.”
Other players are competing in the PQC market. DigiCert, for instance, a 22-year-old firm based in Lehi, Utah, offers its own certificate management platform and claims to provide PQC support. DigiCert employs over 1,600 globally. It also says it has worked with NIST on standards, as well as with other groups, including the IETF.
Other players, just to name a few, include Post Quantum, a company based in London, England, that provides PQC for NATO to help it avoid quantum attacks; and ISARA Corp., which has developed a smart PQC card with Japan’s TOPPAN Digital and National Institute of Information and Communications Technology (NICT).
The PQC Timeframe
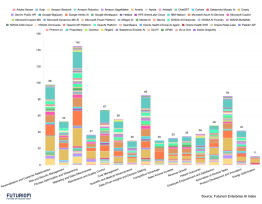
While quantum computing remains a futuristic technology for many enterprises, the fear of post-quantum hacks is growing. In a DigiCert survey of over 1,000 IT professionals worldwide, 69.2% said they expected quantum computers to break encryption within five years, and over one-third believed it could happen within two years.

Source: DigiCert
Futuriom Take: Post-Quantum Cryptography is gaining momentum, as enterprises anticipate the dangers of quantum computers breaking existing RSA and ECC encryption. Expect to see a surge in companies offering solutions — including discovery, which is a crucial step for enterprises.