Why Is Interest in eBPF and Cilium Growing?
The increased role of cloud-native networking, along with momentum around observability, has focused attention on eBPF (extended Berkeley Packet Filter), an open-source, Linux-based technology that provides visibility for security, load balancing, and policy-based networking -- and generally streamlines the speed and efficiency of programs that use Kubernetes-based microservices.
The realities of eBPF are down deep in the depths of Linux-based engineering. But there are several essential and easy-to-grasp facts about this technology:
- It runs inside the kernel of the Linux operating system – meaning the essential, central core of the system that governs the activity of a computer.
- eBPF runs in “sandboxed” fashion inside the Linux kernel. It does not interfere with any of the basic functions of the kernel.
- It is secure because it runs in a privileged context within the Linux kernel.
- eBPF allows the Linux operating system to take on additional capabilities at runtime, such as observability and load balancing.
- eBPF supports an open-source project named Cilium, which adds a layer of abstraction on top of eBPF to make it easier to create programs that add scalability, security, and visibility to container workloads.
Let’s take a closer look at these fundamentals.
Basic Functionality
eBPF originated from Berkeley Packet Filter, a virtual-machine technique that controlled packet filtering from within the Linux kernel for networking purposes. BPF worked in the kernel as opposed to the user space within the Linux operating system. The user space must rely on system calls to manipulate hardware, whereas programs in the kernel space have direct access to resources.
In 2014, additional work resulted in eBPF, which extended the parameters of the original technology significantly – hence the added “e” to eBPF. The technology could now be used to create applications that tracked and even controlled traffic without burdening the application layer. This ensured that eBPF could not only be used for a variety of additional purposes but would scale well. All of this has helped draw interest in eBPF.
eBPF programs are written in a subset of the C programming language. They are then compiled into machine-readable bytecode via LLVM, an open-source technology that offers compilers and toolsets for a variety of programming languages. Once set up, an eBPF application acts as virtual machine that is activated by the kernel in response to events called hooks, which include system calls. Once this happens, eBPF adds capabilities to the operating system at runtime without requiring any recompiling or other activity that would affect the functioning of the OS. Instead, an eBPF-integral Just-In-Time (JIT) compiler is activated to allow the program to run without requiring the kernel to recompile it, and a verification tool is added to ensure security.
Because eBPF runs securely within the Linux kernel, developers must be careful to set up its privileged status while implementing applications. Once that’s done, the JIT and verification engine ensure that programs can run safely.
eBPF programs also have a crucial feature called maps, which is a key value database that allows information to be stored for use at runtime. Maps allow information to be updated and shared between eBPF kernel programs and programs in the Linux user space. This strengthens the functionality of applications.
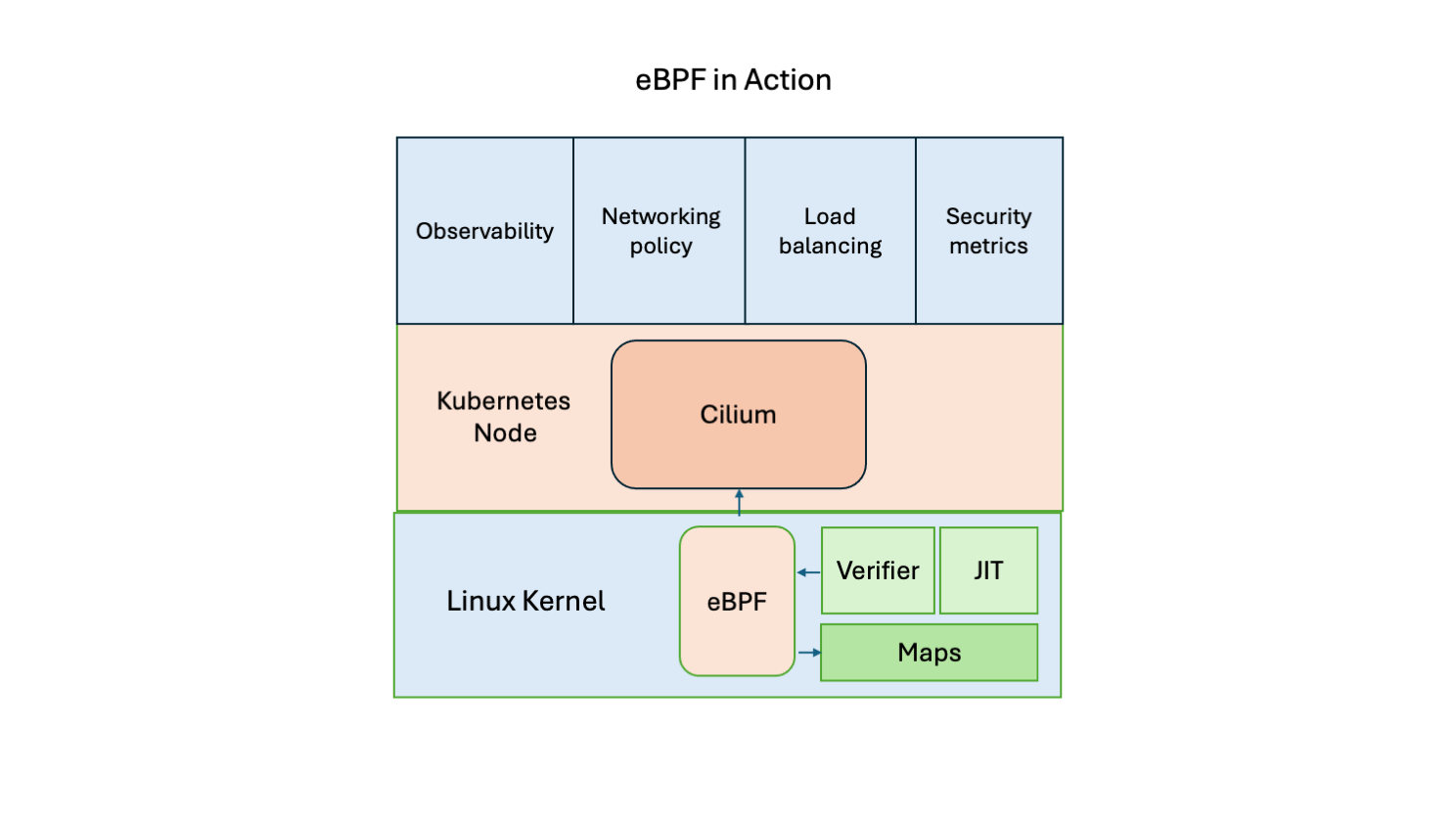
CNIs, eBPF, and Cilium
Interest in eBPF has spawned a series of applications using a Container Networking Interface (CNI). The most popular of these is Cilium, an open-source project that provides a platform for deploying eBPF for networking, security, and observability. It can be used as a “network plugin” for Kubernetes. Competing open-source CNIs for networking applications include Calico and Flannel.
Cilium was founded by Thomas Graf, who became the CTO of Isovalent, the company recently purchased by Cisco. Graf and his team, including CEO Dan Wendlandt, helped bring eBPF to the cloud development mainstream by Isovalent’s contributions to Cilium as well as its commercial implementation of that technology. Cisco will make Isovalent part of its Cisco Security Cloud platform, which uses AI to guard access and maintain network visibility against threats.
There are a range of other applications based on eBPF which can be adapted for use in a variety of ways. These include Falco, which monitors kernel-level system activity to detect anomalous application behavior; Pixie, for observability of Kubernetes applications; and Katran, for load balancing.
eBPF Is Widely Deployed, Despite Drawbacks
Many companies are using eBPF for observability and performance monitoring, security, load balancing, networking, kernel monitoring, GPU monitoring, data collection, and more. Users include Apple, CapitalOne, Cloudflare, Datadog, Doordash, Google, LinkedIn, Meta, Microsoft, Walmart, and Sky, to name just a few. These companies and others have adapted eBPF apps for use in their environments.
eBPF does have its detractors. There are complaints that its reliance on operating system resources makes it tough to scale beyond a certain point; that it doesn’t adhere to real-time event reporting; and that its verifier is vulnerable to security breaches. At the same time, however, the technology has captured a sizable following that continues to develop applications for a variety of use cases, creating a trend that shows no hint of slowing down.




















