Inside Identity-based Security and ZTNA

Yes, zero trust network access (ZTNA) may sound like an oxymoron, but it's now the single most important network security paradigm. We dive deep into this emerging technology in a new Futuriom report: Identity-based Security and Zero Trust Network Access (ZTNA).
Let's start by defining what zero trust means. First of all, zero trust doesn't mean that you should have zero trust in the network. It means that the network should have zero trust in you. At its core, zero trust means that the network needs to use many techniques to verify that applications and users have confirmed their identity and deserve access -- in order to build a defendable and impermeable perimeter between an enterprise network and the rest of the world.
What Is the ZTNA Approach?
There are some key tenets, or approaches, of zero trust. They include the following: 1) All connection requests should be considered potentially hostile, regardless of where they originate; 2) Even approved access should be restricted, with connections being set up based on a policy of least-privilege access; 3) Connections should be continuously monitored and authorization reassessed as appropriate.
In addition, the U.S. National Institute of Standards and Technology (NIST) has gotten in the game. It describes zero trust generally as: “A collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.“ NIST states that a zero-trust strategy is “primarily focused on data and service protection but can and should be expanded to include all enterprise assets (devices, infrastructure, components, applications, virtual and cloud components) and subjects (end users, applications and other non-human entities) that request information from resources.”
Explosion of Companies and Products
Now that we have defined ZTNA, let's examine how it's coming to market. It's true that the marketeers have gotten hold of the term and are bandying it about as the latest cybersecurity magic bullet. But there are legitimate reasons for the trend and its impact on cybersecurity technology.
The cybersecurity community is moving toward ZTNA and software defined perimeter (SDP) architectures as part of a need to automate identity-based access. This is necessary as we move to a cloud world were applications and users are connecting to networks at new scale. None of these connections can be supervised manually anymore.
ZTNA products and services come in many different flavors, but the basic approach will become a key feature of many broad cybersecurity portfolios. They can also be segmented based on the underlying technologies deployed, or they can be based on the use cases they generally support. ZTNA products are not designed to solve every access problem, but they will become a tool in a broader market of integrated network security known as Secure Access Service Edge (SASE).
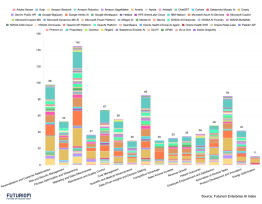
Of course, the excitement has generated investment. As I recently pointed out in a Forbes blog, nearly $8 billion in investment went into cybersecurity companies in 2020 -- much of it into ZTNA products. This has created a veritable land grab as dozens of cybersecurity companies both old and new position their wares toward this architecture.
Our new report lays out the trends in this complicated landscape of identity-based security and ZTNA products and services. We scoped out the the market in detail, taking a look at several different drivers and approaches to ZTNA as well as the products and services of nearly 30 companies.
This report is being offered free to registered subscribers of Futuriom. You can see the highlights of the report below. You can download it here.
Special thanks to our Sponsors: NetFoundry and VMware.
ZTNA Report Highlights
• There is an increase in demand for cybersecurity products to enable identity-based security for providing Zero Trust Network Access (ZTNA). These are products that secure authentication to networks and cloud services, including identity-based security solutions.
• The Zero Trust security model (trusting no one) has evolved as the best practice for securing networking and computing in today’s hybrid environments. The approach is also gaining traction as a response to the rise in the ransomware threat.
• The increase in demand is being driven by expanded use cases for ZTNA and identity-based security for networks and cloud services. Some of the factors include: 1) Increased remote work and the need for virtual network connectivity; 2) An expansion of the enterprise security perimeters, created by the increase in access points and scale of the Internet; and 3) Increased use of cloud-based products and applications (4 billion active users in 2020).
• In the wake of the COVID-19 pandemic, there is strong demand for virtual private network (VPN) augmentation or replacement, which has become the biggest driver for ZTNA deployments.
• Enterprises are finding the need to increase levels of sophistication to control networks and security perimeters. Weakened or nonexistent perimeter protections pose extreme threats to enterprise security.
• The addressable market for ZTNA products and services is over $10 billion. This number would cover a portion of the VPN market, but the upside is much higher.
• ZTNA products are being integrated into packages of broader Secure Access Service Edge (SASE) security solutions. An integrated, cloud-based security suite is the ultimate end goal for many end users, which aligns with a comprehensive zero-trust architecture.
Companies profiled in this report: Absolute Software, Akamai, Appgate, Axis Security,
Banyan Security, Barracuda, Cato Networks, Cisco, Citrix Systems, Cloudflare, Cognitas
Technology, Elisity, Google (BeyondCorp), Juniper Networks, NetFoundry, Netskope, Okta,
OPAQ Networks (For-net), Palo Alto Networks, Perimeter 81, Proofpoint, Versa Networks,
VMware, Wandera, Waverly Labs, Witesand, Zentera Systems, Zscaler