What Is API Security?

In today's digital landscape, APIs (application programming interfaces) have become the backbone of seamless connectivity, enabling businesses to integrate and exchange data, services, and functionalities with ease.
APIs act as intermediaries, allowing different software systems to communicate, share information, and collaborate effectively. From enhancing user experiences to driving innovation, APIs have revolutionized the way applications, platforms, and devices interact and function.
API security focuses on ensuring the protection of data transmitted between clients and servers across public networks. It is also part of the shift left movement. In this Tech Primer, we will explore the significance of securing APIs that are employed in contemporary business operations. We have also covered API security in detail in our Shift Left and API Security report, which also highlights the leading companies in this space.
Significance of API Security
With the potential utilization of APIs in digital businesses, the security of APIs becomes paramount for organizations that adopt them. This security is essential in safeguarding them from potential attacks. Due to their widespread usage and the access they provide to sensitive software functions and data, APIs have become a prime target for attackers.
APIs serve as connectors for businesses, enabling the exchange of services and data. APIs are susceptible to security vulnerabilities originating from backend systems. If an API is compromised, exposed, or hacked, it can lead to the exposure of personal information, financial data, and other sensitive data. As a result, ensuring security becomes an essential aspect to be taken into account when designing and developing various types of APIs, including RESTful APIs.
For instance, a denial of service (DoS) attack can render an API endpoint unavailable or severely degrade its performance. APIs can be exploited by malicious actors through actions such as data scraping or exceeding usage limits. More advanced attackers may inject malicious code to carry out unauthorized operations or compromise the backend infrastructure.
There are other types of common attacks mounted on APIs. These include:
BOLA attacks. Broken Object-Level Authorization (BOLA) attacks occur when object-level references are altered in an API request. This allows attackers to gain access to unauthorized objects or data.
API misconfiguration attacks. Third-party misconfigurations occur when an API is exposed by a third-party and misconfigured, leading to a security vulnerability.
Shadow and zombie APIs. Zombie APIs refer to undocumented APIs existing in an organization's IT footprint. They may have been created by in-house developers or third parties and are no longer actively monitored. These APIs could still be used to access sensitive data or executive functions.
Injection attacks. Injection attacks occur when an attacker sends a malicious input, such as a string of code or data to a web application, to change the operation.
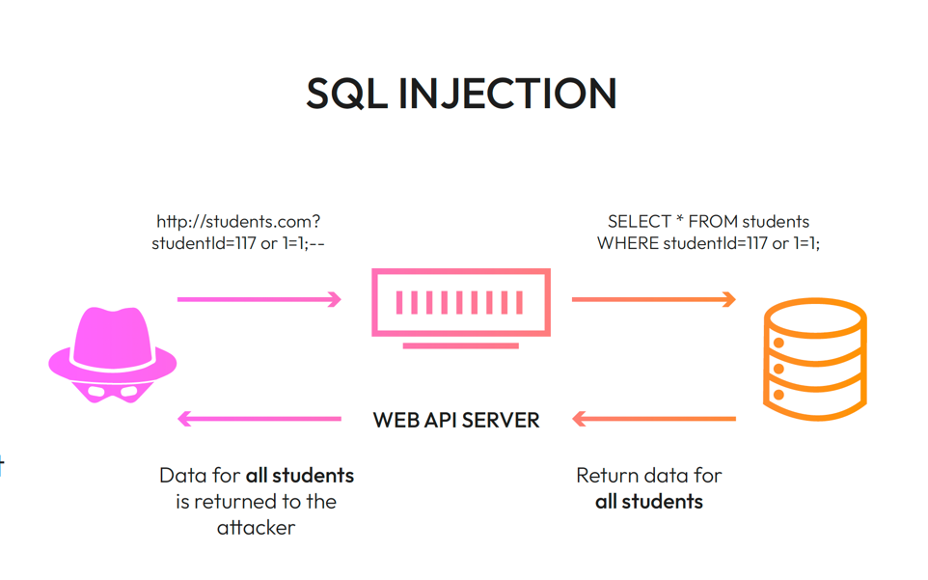
Source: Wib Security
API security plays a vital role in ensuring the overall security of modern applications. APIs may have weaknesses, including issues with authentication and authorization, lack of rate limiting, and vulnerability to code injection.
Given the widespread adoption of microservices and serverless architectures, APIs have become integral to the basic functionality of nearly every enterprise application. Consequently, API security has become a fundamental aspect of modern information security.
Key Components of API Security
API security entails the implementation of diverse measures aimed at guaranteeing the privacy, integrity, and accessibility of data transmitted via APIs. It includes protection against unauthorized access, data breaches, injection attacks, and other forms of exploitation. By addressing potential vulnerabilities and adopting security best practices, organizations can mitigate risks and maintain the integrity of their APIs.
The key components of API security encompass various measures and practices aimed at safeguarding APIs from potential threats and vulnerabilities. These components include:
API inventory and compliance: It's important that an organization have a complete inventory and knowledge of APIs running in the IT footprint. They will need to use tools that track and maintain compliance of API inventory.
Authentication and authorization: The means implementing mechanisms to verify the identity of API users and control their access to resources and functionalities based on their permissions and privileges.
Encryption: Employing encryption protocols (such as HTTPS) to secure data transmission over the network, ensuring that sensitive information remains confidential and protected from unauthorized access.
Input validation and output filtering: Validating and sanitizing API inputs to prevent injection attacks, ensuring that user-supplied data is safe and free from malicious code. Additionally, filtering API outputs helps prevent the inadvertent exposure of sensitive information.
Rate limiting and throttling: Implementing controls to limit the number of requests or transactions from a single client or IP address, preventing abuse and protecting the API from performance degradation or denial-of-service (DoS) attacks.
Access controls: Enforcing granular access controls to restrict API usage to authorized individuals or systems, ensuring that only authenticated and authorized entities can interact with the API.
Secure error handling: Implementing appropriate error handling mechanisms that do not disclose sensitive information in error messages, preventing potential information leakage that could be exploited by attackers.
Logging and monitoring: Implementing robust logging and monitoring systems to track API activity, detect anomalies, and provide a comprehensive audit trail for security analysis and incident response.
API gateway and firewall: Utilizing an API gateway or firewall to serve as a protective layer between the API and external networks, enabling traffic filtering, request validation, and other security controls.
Regular security audits and penetration testing: Conduct routine security audits and penetration testing to identify vulnerabilities, weaknesses, and potential entry points for attackers. This helps organizations proactively address security gaps and ensure ongoing API protection.
By addressing these key components and adopting a comprehensive approach to API security, organizations can enhance the integrity, confidentiality, and availability of their APIs, fostering trust among users and mitigating potential security risks.
Summary
Ensuring the security of APIs is essential to protect sensitive data, preserve customer confidence, adhere to regulations, and mitigate the risk of financial losses or harm to reputation. By giving priority to API security measures, businesses can fortify the resilience and dependability of their systems in today's interconnected digital environment. Regularly conducting API security testing and applying established best practices are imperative for organizations to identify and rectify vulnerabilities effectively.
Some of the leading companies in this space include: Cequence, HiddenLayer, Neosec (Akamai), Noname Security, Salt Security, Orca Security, SentinelOne, Wib, and Wiz. They are all included in our report on API security.





















